Secure MCP servers local deployment
Lock Down Your Node.js App: A Step-by-Step Guide to Safer Coding with AppArmor
Most MCP (Model Context Protocol ) servers are hosted as open-source repositories on GitHub. When you install them on your system—whether through Claude Desktop, Cursor, or our clients —you're essentially downloading and executing remote source code. In my case, I'm running this on Ubuntu.
Since these repositories often have multiple contributors and frequent updates, blindly executing remote code can be risky. Regardless of whether you're using MCP servers or not, you should always follow these critical security practices:
Never Run NPX as Root : Avoid using
sudo npxat all costs.Isolate Your MCP Server Installation : Keep your MCP server files in a dedicated directory, separate from other projects.
By following these hardening precautions, you significantly reduce the risk of accidental system-wide damage. For more secure minded and learn a few tools, I use ChatGPT and DeepSeek to write the follow steps on limiting access rights of nodeJS process on Linux. Ubunutu ships AppArmor and installed by default. AppArmor reads a security profile and following the rules in the profile, operates in two modes AUDIT (use cmd aa-complain ) and ENFORCE ( use cmd aa-enforce). You shall use audit and check for DENIED in logs before change to ENFORCE.
In my case, with 4 MCP servers installed in a dedicated folder there is no DENIED. The codes has read only access to some system commands and the NodeJS folders.
In this guide, you’ll learn how to set up AppArmor step-by-step, even if you’re new to Linux security. Let’s make your Node.js projects safer! At the end I also share a LLM prompt to generate your own security profile.
1. What is AppArmor? (In Plain English)
AppArmor is a security tool for Linux that lets you create “rulebooks” for your apps. Think of it like a parent setting boundaries for a child:
File Access: “You can only read/write files in THIS folder.”
Network Rules: “You can’t connect to random websites.”
Activity Logs: “Tell me every time you try to break the rules.”
Why It Matters: If a Node.js package tries to access your photos or connect to a suspicious server, AppArmor blocks it and alerts you.
2. Step-by-Step: Setting Up AppArmor for Node.js
📥 Step 1: Install AppArmor (If Missing)
Most Ubuntu systems have AppArmor preinstalled. Check with:
sudo systemctl status apparmor If it’s not installed, run:
sudo apt update && sudo apt install apparmor apparmor-utils
sudo systemctl enable apparmor --now ⚙️ Step 2: Create a Security Profile for Node.js
What You’ll Do: Create a rulebook that says, “My Node.js app can ONLY access these files and networks.”
Open a New Profile File:
sudo nano /etc/apparmor.d/node-appPaste These Rules (Customize Paths to Match Your Setup):
# Allow basic system functions #include <abstractions/base> # Let Node.js run your project /home/your-username/my-node-project/** rwix, # Allow network connections (but log them) audit network, # Block risky actions deny /etc/shadow r, # No reading sensitive system files deny /home/*/ssh/** rw, # No touching SSH keysKey Symbols Explained:
rwix: Read, Write, Execute files in your project.audit network: Log all internet connections.
🧪 Step 3: Test Your Rules (Without Blocking Anything)
Before enforcing rules, test them in “complain mode” to catch mistakes:
Load the Profile:
sudo apparmor_parser -r /etc/apparmor.d/node-app sudo aa-complain /etc/apparmor.d/node-appRun Your Node App:
node /home/your-username/my-node-project/index.jsCheck Logs for Warnings:
tail -f /var/log/syslog | grep "apparmor"If you see errors like
DENIED, adjust your profile to allow necessary actions.
🔒 Step 4: Enforce Your Rules
Once testing is done, turn on strict blocking:
sudo aa-enforce /etc/apparmor.d/node-app Now, AppArmor will block any action not in your rulebook!
3. Monitoring Suspicious Activity
🌐 Example: Catch Hidden Network Connections
AppArmor logs every connection your app makes. To see where your app is “phoning home”:
sudo grep 'apparmor="AUDIT"' /var/log/syslog | grep 'faddr=' Look for strange IPs or domains. For example, if your weather app tries to connect to a crypto miner’s server, you’ll see it here!
📂 Example: Block Unauthorized File Access
If a package tries to read your SSH keys, AppArmor logs:
apparmor="DENIED" operation="open" path="/home/you/.ssh/id_rsa" Action: Investigate the offending package immediately!
4. Extra Protection: Restrict Internet Access
Problem: Your app only needs to connect to api.yourservice.com, but a bad package tries to call evil-server.com.
Solution: Tighten network rules in your profile:
# Allow ONLY IPv4 and block everything else
network inet,
deny network inet6,
deny network netlink, 5. Automate Log Cleanup
Too many logs? Set up automatic log rotation:
Create a Config File:
sudo nano /etc/logrotate.d/apparmor-nodeAdd These Rules:
/var/log/syslog { rotate 7 daily compress delaycompress missingok }
Now, logs older than 7 days get deleted automatically!
6. LLM Prompts to generate AppArmor security profile using adpting to your paths
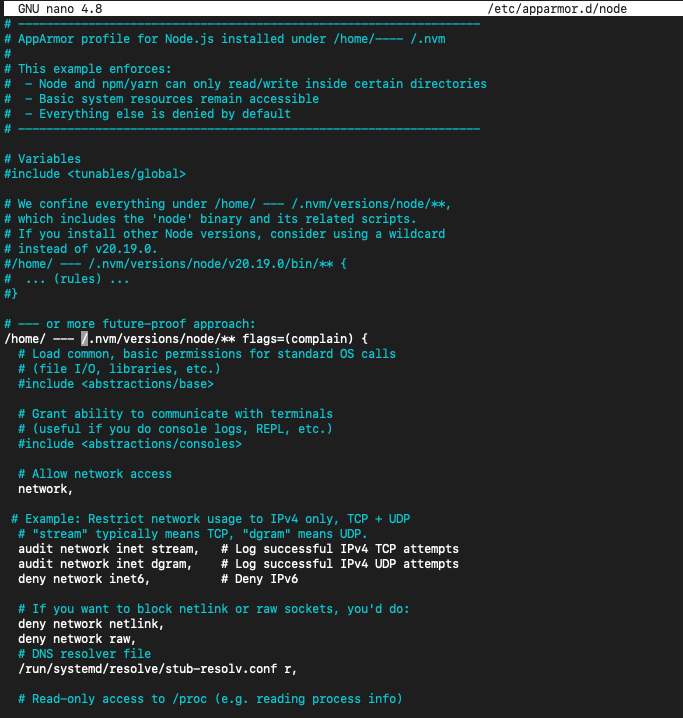
Generate a moderate security level AppArmor profile for my environment, where the home directory is /home/user-1 and the Node.js installation directory is located at /path/to/node or under nvm. MCP servers are installed at /opt/path-of-mcp
# Variables
#include <tunables/global>
# We confine everything under /home/---- /.nvm/versions/node/**,
# which includes the 'node' binary and its related scripts.
# If you install other Node versions, consider using a wildcard
# instead of v20.19.0.
#/home/----/.nvm/versions/node/v20.19.0/bin/** {
# ... (rules) ...
#}
# --- or more future-proof approach:
/home/----/.nvm/versions/node/** flags=(complain) {
# Load common, basic permissions for standard OS calls
# (file I/O, libraries, etc.)
#include <abstractions/base>
# Allow network access
network,
# Example: Restrict network usage to IPv4 only, TCP + UDP
# "stream" typically means TCP, "dgram" means UDP.
audit network inet stream, # Log successful IPv4 TCP attempts
audit network inet dgram, # Log successful IPv4 UDP attempts
deny network inet6, # Deny IPv6
# If you want to block netlink or raw sockets, you'd do:
deny network netlink,
deny network raw,
# DNS resolver file
/run/systemd/resolve/stub-resolv.conf r,
# Read-only access to /proc (e.g. reading process info)
/proc/** r,
# Read system config (like /etc/hosts, /etc/ssl/..., etc.)
/etc/** r,
# Execute system binaries (e.g. git, bash, etc.) if needed
/bin/** ix,
/usr/bin/** ix,
# NPM & Yarn caches, config files
/home/----/.npm/** rwl,
/home/----/.yarn/** rwl,
/home/----/.cache/yarn/ rwl,
/home/----/.cache/yarn/** rwl,
/home/----/.npmrc rw,
/home/----/.yarnrc rw,
# REPL history (so node CLI can save history)
/home/----/.node_repl_history rw,
# Temporary files
/tmp/ rw,
/tmp/** rw,
# Allow read/write/execute access to the Node install tree itself
# (the 'l', 'k', 'm' flags allow linking, locking, and mounting if needed)
/home/----/.nvm/versions/node/** rwixlm,
# Development directory (where your app lives)
# 'rwixlkm' = read, write, inherit execute, link, lock, m (mount)
/opt/----/mcp-wa/** rwixlkm,
# ConfigStore usage (some Node modules store user-level configs here)
/home/----/.config/configstore/ rw,
/home/----/.config/configstore/** rw,
}
Reference : https://dmitrychekanov.com/posts/securing-node-js-development-environment-with-app-armor/
https://www.digitalocean.com/community/tutorials/how-to-set-up-a-node-js-application-for-production-on-ubuntu-20-04
Questions? Drop a comment below! 👇